PERMISSIONS Administrators
NAVIGATION File Protection Online > Team > Security
NOTE Ransomware detection is supported on File Protection Server and File Protection Desktop for Windows and Mac 7.4 or later, and malware detection is supported in all versions. We recommend that you use the most recent versions to enjoy the best possible user experience.
About security monitoring
File Protection's Security Incident Detection and Management feature:
-
Uses a series of complex algorithms to detect ransomware attacks and Symantec Endpoint Protection to detect malware attacks.
- Automatically quarantines and deletes affected files.
- Provides you with a confidence rating for ransomware security incidents.
- Allows you to manage each incident.
-
Streamlines reversion of all affected files to their state before the attack.
- Automatically notifies all Administrators or selected users of security incidents.
- (Ransomware only) Provides you with a mechanism to ignore an incident report from certain devices, or to place one or more devices on a Security Excluded Devices list to avoid repeated false positive incident reports.
You'll use both the Security page, described below, and the Ransomware Incident detail and Malware Incident detail pages to monitor and manage the entire process from initial incident detection from initial incident detection through all applicable recovery steps.
IMPORTANT If you have a confirmed ransomware incident, we recommend that you revert the affected files, recycle the device via File Protection, completely uninstall File Protection from the device (refer to Install or uninstall File Protection Desktop), scrub the device of all malware, reinstall File Protection, and restore the files from the service.
The Security page
On the Security page, you'll be able to configure security monitoring, review security incidents and the files they've affected, and track devices that have been exempted from monitoring.
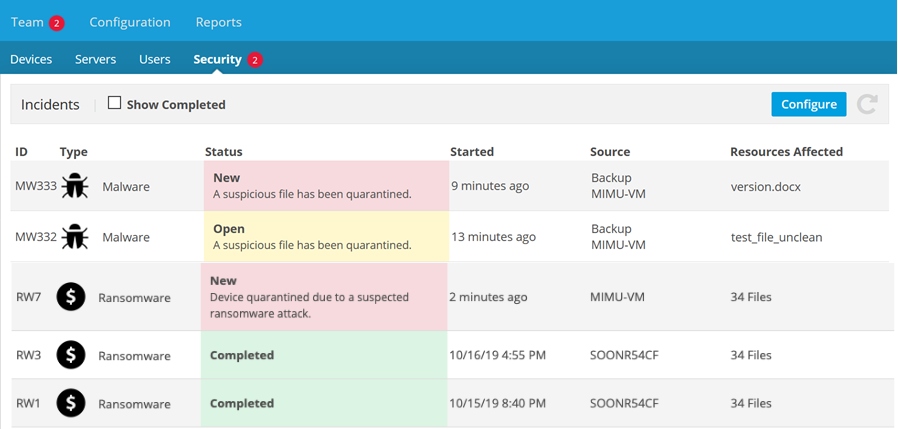
The Incident grid
The Incident grid displays all security incidents detected.
NOTE Only active incidents (incidents with a status that is not Complete) are displayed by default. To display all incidents, select the Show Completed check box at the top left of the grid.
This grid features the following columns:
| Column | Definition |
|---|---|
| ID | The system-generated identification code for the specific incident. The first two characters indicate the type of incident. This ID ensures clear communication when discussing incidents. |
| Type | The classification of the incident. The icon helps identify the type at a glance. |
| Status | The current state of the alert. Available statuses are: New Open Ignored (ransomware only) Completed |
| Started | The time at which File Protection first detected suspicious activity. |
| Source |
For ransomware incidents, the name of the quarantined device. For malware incidents, information about the suspicious file. |
| Resources Affected |
For ransomware incidents, the number of files affected by the incident. For malware incidents, the name of the affected file. |
The Security Excluded Devices grid
The Security Excluded Devices grid, which applies to ransomware detection only, displays all devices that have been temporarily or permanently removed from security incident monitoring. It features the following columns:
| Column | Definition |
|---|---|
| Device | The name and operating system of the excluded device. |
| Owner | The user associated with the excluded device. |
| Excluded | The time at which the device was excluded from security monitoring. |
| Excluded By | The user who excluded the device from security monitoring. |
How to...
- Click the Configure button. This will open the configuration pane:
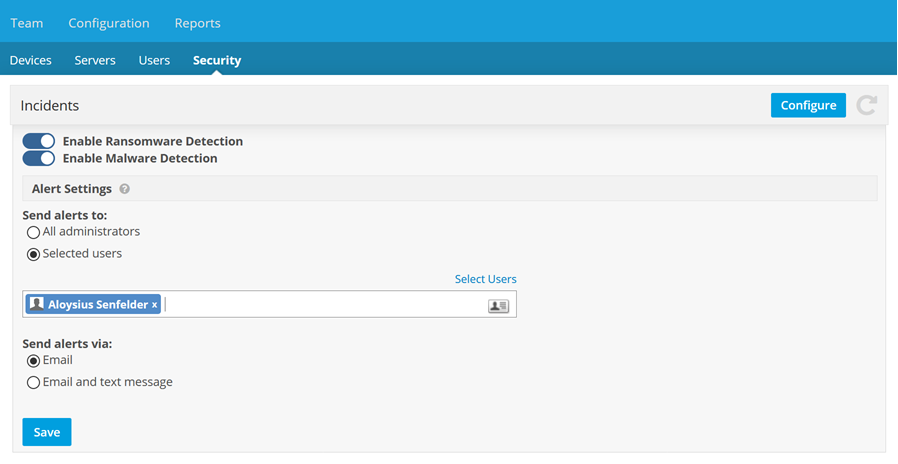
- Use the toggles to enable or disable each security feature.
- Use the radio buttons to select a Send alerts to option. If you choose Select users, the pane will expand. Type a name or email address to find recipients, or use the Pick From Team link or
 icon to open a selection window.
icon to open a selection window.
- Use the radio buttons to select a Send alerts via option.
- Click Save.
Click the incident you wish to view. Depending on the type of security incident, his will open the Ransomware Incident detail page or the Malware Incident detailf page for that item.